Credit:
IC3.gov
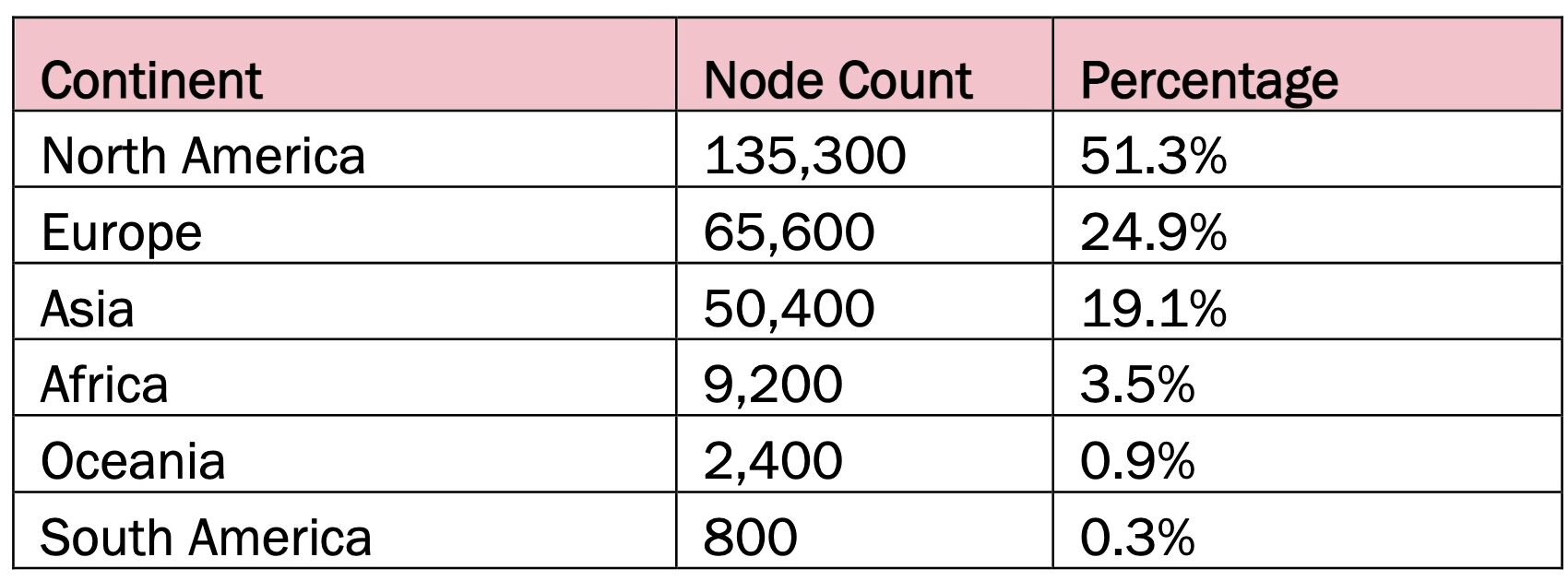
Raptor Train concentration by continent.
Credit:
IC3.gov
Credit:
IC3.gov
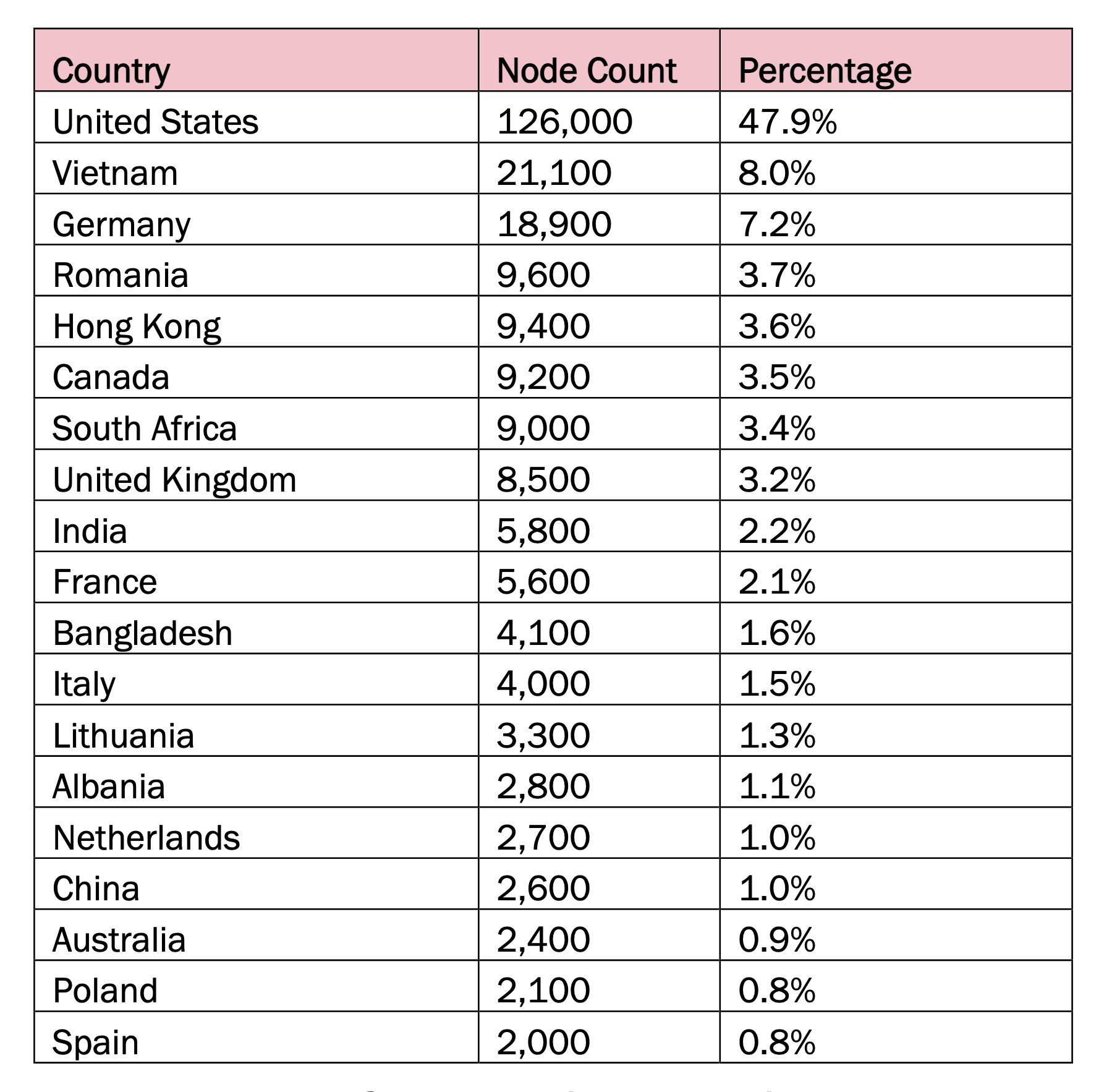
Raptor Train concentration by country.
Credit:
IC3.gov
“Flax Typhoon was targeting critical infrastructure across the US and overseas, everyone from corporations and media organizations to universities and government agencies,” FBI Director Christopher Wray said Wednesday at the Aspen Cyber Summit. “Like Volt Typhoon, they used Internet-connected devices, this time hundreds of thousands of them, to create a botnet that helped them compromise systems and exfiltrate confidential data.” He added: “Flax Typhoon’s actions caused real harm to its victims who had to devote precious time to clean up the mess.”
Wray said law enforcement agents sought and executed court-authorized operations that took control of the Raptor Train infrastructure. Like the operation in January, it worked by identifying compromised devices and surreptitiously issuing commands that disinfected them of the Raptor Train malware.
“When the bad guys realized what was happening, they tried to migrate their bots to new servers and even conducted a DDoS attack against us,” Wray said. “Working with our partners, we were able to not only mitigate their attack but also identify their new infrastructure in just a matter of hours. At that point, as we began pivoting to their new servers, we think the bad guys finally realized it was the FBI and our partners that they were up against, and with that realization they essentially burned down their new infrastructure and abandoned their botnet.”
Operating at scale
Black Lotus Labs, the security research arm of Lumen Technologies, has been tracking Raptor Train since June 2023. In an 81-page report also published Wednesday, the researchers said the botnet, four years in the making, was so large that it landed on both the Cloudflare Radar and the Umbrella Popularity List compiled by Cisco.
The heft is the result of a sophisticated, multi-tier structure that allows the botnet to operate at a massive scale. If Raptor Train were a pyramid, its bottom, largest section would be made up of Tier 1. This tier comprises home and small office devices that are infected with “Nosedive,” custom malware that’s based on Mirai, a family of IoT-optimized malware that delivered record-setting DDoSes when it burst on the scene in 2016 and was released as open source that same year.




