Credit:
Proofpoint
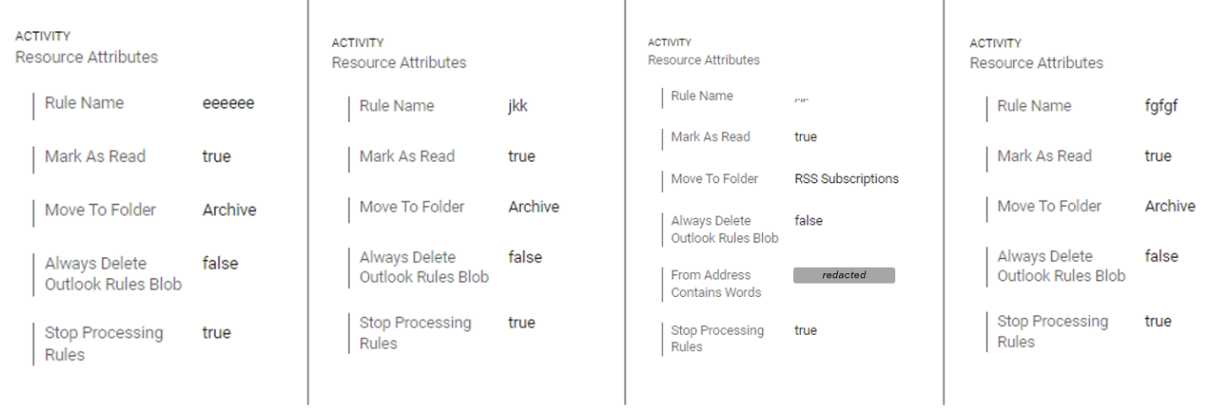
Examples of obfuscation mailbox rules created by attackers following successful account takeover.
Credit:
Proofpoint
The compromises are coming from several proxies that act as intermediaries between the attackers’ originating infrastructure and the accounts being targeted. The proxies help the attackers align the geographical location assigned to the connecting IP address with the region of the target. This helps to bypass various geofencing policies that restrict the number and location of IP addresses that can access the targeted system. The proxy services often change mid-campaign, a strategy that makes it harder for those defending against the attacks to block the IPs where the malicious activities originate.
Other techniques designed to obfuscate the attackers’ operational infrastructure include data hosting services and compromised domains.
“Beyond the use of proxy services, we have seen attackers utilize certain local fixed-line ISPs, potentially exposing their geographical locations,” Monday’s post stated. “Notable among these non-proxy sources are the Russia-based ‘Selena Telecom LLC’, and Nigerian providers ‘Airtel Networks Limited’ and ‘MTN Nigeria Communication Limited.’ While Proofpoint has not currently attributed this campaign to any known threat actor, there is a possibility that Russian and Nigerian attackers may be involved, drawing parallels to previous cloud attacks.”
How to check if you’re a target
There are several telltale signs of targeting. The most helpful one is a specific user agent used during the access phase of the attack: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Attackers predominantly utilize this user-agent to access the ‘OfficeHome’ sign-in application along with unauthorized access to additional native Microsoft365 apps, such as:
- Office365 Shell WCSS-Client (indicative of browser access to Office365 applications)
- Office 365 Exchange Online (indicative of post-compromise mailbox abuse, data exfiltration, and email threats proliferation)
- My Signins (used by attackers for MFA manipulation)
- My Apps
- My Profile
Proofpoint included the following Indicators of compromise:
| Indicator | Type | Description |
| Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 | User Agent | User Agent involved in attack’s access phase |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 | User Agent | User Agent involved in attack’s access and post-access phases |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 | User Agent | User Agent involved in attack’s access and post-access phases |
| sachacel[.]ru | Domain | Domain used for targeted phishing threats |
| lobnya[.]com | Domain | Source domain used as malicious infrastructure |
| makeapp[.]today | Domain | Source domain used as malicious infrastructure |
| alexhost[.]com | Domain | Source domain used as malicious infrastructure |
| mol[.]ru | Domain | Source domain used as malicious infrastructure |
| smartape[.]net | Domain | Source domain used as malicious infrastructure |
| airtel[.]com | Domain | Source domain used as malicious infrastructure |
| mtnonline[.]com | Domain | Source domain used as malicious infrastructure |
| acedatacenter[.]com | Domain | Source domain used as malicious infrastructure |
| Sokolov Dmitry Nikolaevich | ISP | Source ISP used as malicious infrastructure |
| Dom Tehniki Ltd | ISP | Source ISP used as malicious infrastructure |
| Selena Telecom LLC | ISP | Source ISP used as malicious infrastructure |
As the campaign is ongoing, Proofpoint may update the indicators as more become available. The company advised companies to pay close attention to the user agent and source domains of incoming connections to employee accounts. Other helpful defenses are employing security defenses that look for signs of both initial account compromise and post-compromise activities, identifying initial vectors of compromise such as phishing, malware, or impersonation, and putting in place auto-remediation policies to drive out attackers quickly in the event they get in.